Summary
Hackers Victim is a 14 (character(s) / byte(s)) length name. It consist of 2 word(s). There are 9 consonant(s) and 4 vowel(s) in Hackers Victim. Its characters by alphabetic order: H, V, a, c, c, e, i, i, k, m, r, s, t. Its Soundex Index is H262, and Metaphone value is HKRSFKTM. "Hackers Victim" is a short name.
Writing in different systems
| System name | Value |
|---|---|
| Name full length: | 14 characters (14 bytes) |
| Repeating characters: | - |
| Decimal name: | 1001000 |
| Binary name: | 0100100001100001011000110110101101100101 ... |
| ASCII name: | 72 97 99 107 101 114 115 32 86 105 99 11 ... |
| HEX name: | 4800610063006B00650072007300200056006900 ... |
| Name with Morse: | .... .- -.-. -.- . .-. ... ...- .. -.-. - .. -- |
Character architecture chart
Conversions
| Type | Data (only english letters get processed) |
|---|---|
| Hackers Victim with Greek letters: | (h) α χ κ ε ρ σ (v) ι χ τ ι μ |
| Hackers Victim with Hindi letters: | (h) अ च क ए र स व इ च ट इ म |
| Hackers Victim with Chinese letters: | 艾尺 诶 西 开 伊 艾儿 艾丝 维 艾 西 提 艾 艾马 |
| Hackers Victim with Cyrillic letters: | х a ц к e р с в и ц т и м |
| Hackers Victim with Hebrew letters: | ה (a) ק(c) ק(k) (e) ר שׂ ו (i) ק(c) ת (i) מ |
| Hackers Victim with Arabic Letters: | ح ا (c) ك (e) ر ص (v) (i) (c) ت (i) م |
|
Name pattern:
V: Vowel, C: Consonant, N: Number
| C V C C V C C C V C C V C |
| Letter position in alphabet: | h8 a1 c3 k11 e5 r18 s19 v22 i9 c3 t20 i9 m13 |
| Name spelling: | H A C K E R S V I C T I M |
| Name Smog Index: | 1.8449900557727 |
| Automated readability index: | 10.185 |
| Gunning Fog Index: | 0.8 |
| Coleman–Liau Index: | 22.335 |
| Flesch reading ease: | 35.605 |
| Flesch-Kincaid grade level: | 8.79 |
How to spell Hackers Victim with hand sign












Numerology
| Letters in Chaldean Numerology | 5 1 3 2 5 2 3 6 1 3 4 1 4 |
| Chaldean Value | 40 |
Vowel meaning in the name Hackers Victim
The First Vowel of your name represents the dreams, goals, and urges which are the forces that keep you going from behind the scenes. This letter represents the part of you that is difficult for others to find out about. This letter sheds more light on the inner workings of your soul, and only a few of those closest to you may have an idea about it. These people may be members of your family or some of your closest friends. Some people may not like who they are on the inside, and this may lead them to change this letter. It is quite uncommon to meet such a person.
Capstone (last letter): The letter which ends your name is known as the Capstone. Being the letter which ends your name, it also bears a similar effect on discerning your potential to complete an undertaken. By combining your Cornerstone and Capstone, you can discover the ease with which you can begin and end any project or idea. The Capstone can help identify if you are influential or active, or if you can be unreliable or a procrastinator.
Last Letter in Hackers Victim, The meaning of "m": You work hard and long while you possess the energy to achieve this. Your body remains in good health, and you do not require a lot of sleep to function efficiently. You also prefer to stay at home and may develop a sense of insecurity if you don't have a reliable means of income. Avoid getting annoyed with others due to your desire to achieve your goals.| MD5 Encoding: | a8244cdbb5dd7d31fe8aa91fa42ddc54 |
| SHA1 Encoding: | 71d40b1dbcc34e0ffe29334a859d184d719c232b |
| Metaphone name: | HKRSFKTM |
| Name Soundex: | H262 |
| Base64 Encoding: | SGFja2VycyBWaWN0aW0= |
| Reverse name: | mitciV srekcaH |
| Number of Vowels: | 4 |
| Name without english Vowels: | Hckrs Vctm |
| Name without english Consonant: | ae ii |
| English letters in name: | HackersVictim |
|
Unique Characters and Occurrences:
"Letter/number": occurences, (percentage)
| "H": 1 (7.69%), "a": 1 (7.69%), "c": 2 (15.38%), "k": 1 (7.69%), "e": 1 (7.69%), "r": 1 (7.69%), "s": 1 (7.69%), "V": 1 (7.69%), "i": 2 (15.38%), "t": 1 (7.69%), "m": 1 (7.69%), |
| Letter Cloud: | H a c k e r s V i t m |
| Alphabetical Order: |
H, V, a, c, c, e, i, i, k, m, r, s, t
|
|
Relative frequencies (of letters) by common languages*
*∑: English, French, German, Spanish, Portuguese, Esperanto, Italian, Turkish, Swedish, Polish, Dutch, Danish, Icelandic, Finnish, Czech
|
a: 8,1740% c: 2,1083% e: 11,5383% i: 7,6230% k: 2,3224% m: 3,0791% r: 6,5587% s: 6,0311% t: 5,9255% |
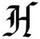
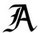
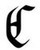
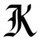
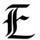
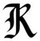
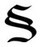
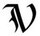
Interesting letters from Hackers Victim